Securitate
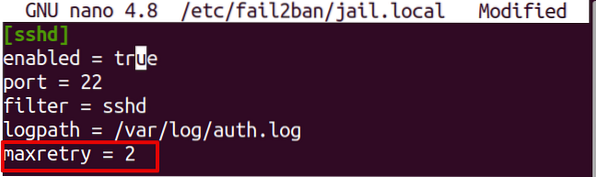
Cum să schimbați timpul de interzicere fail2ban, chiar interziceți definitiv dacă doriți
Fail2ban este un serviciu de prevenire a intruziunilor open-source care interzice adresele IP, făcând prea multe încercări de conectare cu o parolă gr...
How to unban an IP in fail2ban
Many of the security tools do not protect your system from compromise. Even setting the strongest password does not solve the problem as it can also b...
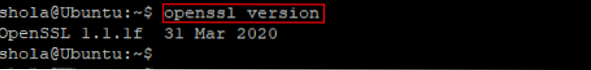
How Do I Create a .CRT File in Linux?
Files with the .CRT extensions are normally SSL/TLS certificates. The .CRT extension is one of the most commonly used SSL/TLS certificate formats in L...
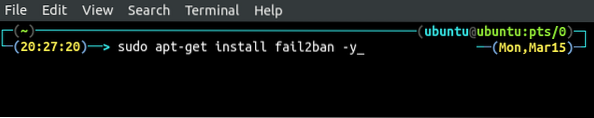
Cum se configurează un IPS (Fail2ban) pentru a fi protejat de diferite atacuri
IPS sau sistemul de prevenire a intruziunilor este o tehnologie utilizată în securitatea rețelei pentru a examina traficul de rețea și a preveni difer...
SQL Truncation Attack
The SQL Truncation vulnerability occurs when a database truncates the user input due to a restriction on the length. Attackers can gather information ...
Top 10 Most Secure Linux Distros for Personal Use
It is no secret that everyone looks for a secure operating system that offers top-notch privacy. If you are using a system that is not secure enough, ...
How to recon Domains and IPs with Spyse toolset
Reconnaissance, shortly termed as recon, refers to the set of related activities and techniques to gather the information of a target system. For inst...
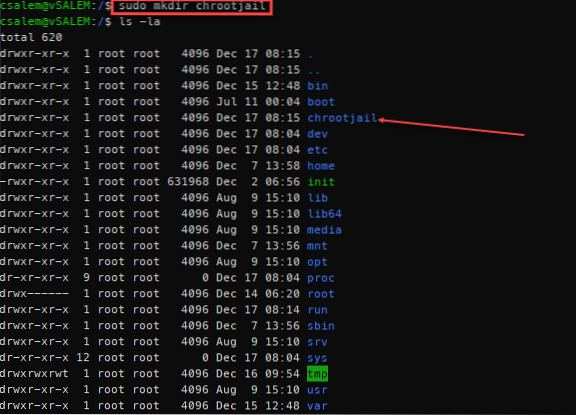
How To Setup Linux Chroot Jails
Especially those dedicated to critical services, Linux systems require expert-level knowledge to work with and core security measures. Unfortunately,...
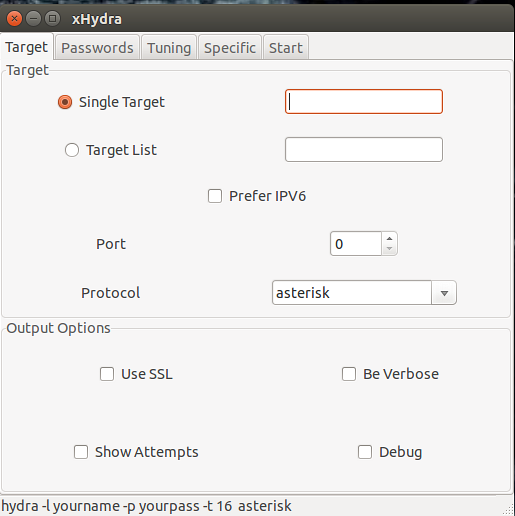
How to install and use THC Hydra?
Passwords are the weakest links. If someone gets ahold of your password, it's game over! As such, passwords are the most important security weaknesses...
 Phenquestions
Phenquestions