Bash is the basic shell of UNIX, a language that is used on many platforms: from different web hosting servers to modems, toys etc. If you are a Windows user, you need not fear ShellShock vulnerability as the chances of your being affected are near nil. But if you have been visiting websites that host themselves on UNIX servers, or use goods that employ UNIX for functioning, you may fall prey to malware or something similar that might harm you in some way. This article tries to explain Bash Vulnerability or ShellShock as it is called, in a layman's terms.
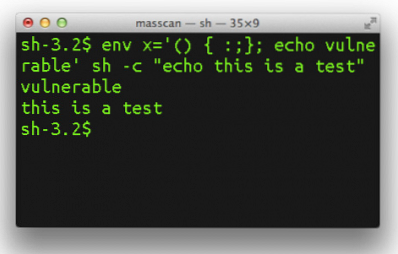
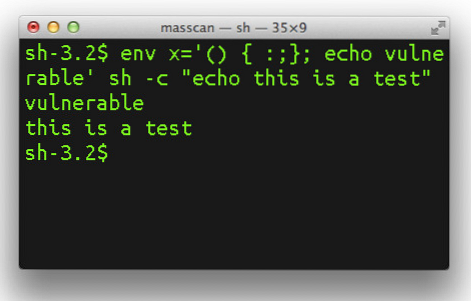
What is BASH
UNIX is basically a command line operating system. Though there are many variations that offer GUI (Graphical User Interface), the base of such interfaces is the Command Line Interface (CLI) of UNIX. And UNIX is everywhere from web hosting servers to the “things” in the Internet Of Things. There are objects like connected microwave that communicates in UNIX rather than using any other operating system as UNIX is easier to install and is considered safer (that is, until the Bash Vulnerability appeared).
UNIX is also a light weight operating system and has literally hundreds of commands that it deals with, to produce proper output - whether working directly on the Command Line Interface or on a GUI that is based on the Command Line Interface.
Coming to BASH, it is an inseparable part of UNIX: It is the shell of UNIX. I mean to say that it is that part of UNIX that takes in commands and processes them to provide you with the desired output irrespective of whether that command was given directly by a user or was sent to the shell using some sort of GUI.
ShellShock or Bash Vulnerability
This section talks about what exactly is the vulnerability in UNIX that has the industry feel threatened. Normally, on a command line, there are many things that happen. For example, values of different parameters are passed that are processed by the computer without checking the source of values. Each command has a command name, switches and command parameters. Like for example, in MS DOS Type command, you have the command syntax as:
Type filename.txt /p [>textfile.txt|print]
Here, the filename.txt and textfile.txt are parameters that define which file to view or print. Or to store output into textfile.txt. Commands are similar in UNIX in a manner that they too have parameters and UNIX does not care where the parameters come from as long as the syntax is correct. Same applies to any command line interface programs and operating systems.
Now, coming to the vulnerability, malicious users can pass malicious parameters to any UNIX command with an intention to exploit this weakness of the command line operating system. The malicious users can pass off devastating things as commands or as command parameters without UNIX knowing that it is about to destroy the computer it is working on.
Some experts say the values of environmental variables can also affect the computers. Environmental variables are values that are used by operating system to perform specific tasks, much like the commands but the values here are global and not specific to a command.
Being a part of the very shell, the vulnerability is also known as Shellshock and is hard to deal with. I am not sure how the different companies using UNIX are to address this vulnerability as it is based on huge weakness. It will take a great deal of thinking and probably scanning each command (that might slow down systems).
ShellShock Vulnerability Scanner
Run this on-demand scanner from TrendMicro on your Linux systems to determine if the BashLite malware is resident. Scan your website to assess whether it is vulnerable to the ShellShock or the Bash vulnerability.
Patches for Bash Vulnerability
The National Vulnerability Database lists some patches that might help UNIX users to some extent, but I suppose that does not do away all the problems associated with the Bash Vulnerability. This has to be worked upon by the experts in the fields of UNIX programming and it might take some time before a proper fix is issued to patch up the vulnerability forever. Till then, computers and automated devices using UNIX will still be at risk and might pose risk to other devices and computers connected to them.
 Phenquestions
Phenquestions