Microsoft published a new out of band security bulletin today that informs about a newly detected critical security vulnerability in the company's Internet Explorer web browser.
The vulnerability, which is already exploited in the wild according to the company, affects Internet Explorer 7 to 11 on client and server operating systems. Microsoft Edge, the default Windows 10 web browser, is not listed on the page and thus not affected by the vulnerability.
The vulnerability is rated critical for all client operating systems and moderate for all server operating systems of the company.
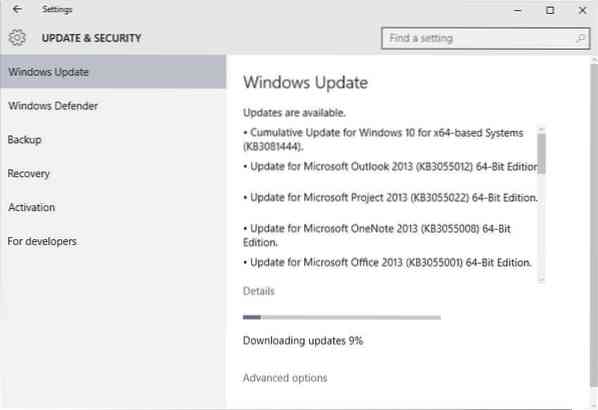
Microsoft released patches for all affected (and supported) versions of Windows. These patches are already available via Windows Update and via Microsoft's Download Center.
The update is listed as "cumulative update for Windows 10 (KB3081444)" for Windows 10 systems, and listed with the code KB3087985 on previous versions of Windows. The update KB3078071 is a prerequisite for that update on Windows 8.1 and 7, and Windows Server 2008 R2 and 2012 R2.
Attackers can exploit the vulnerability by through various means, for instance by creating web pages that exploit the vulnerability, HTML emails or web advertisement. All that is needed to trigger the vulnerability is that these contents get loaded in an affected version of Internet Explorer, an interaction with the site is not required apart from that.
Attackers gain the same rights as the current user on the system. If the logged in user has administrative rights, a complete takeover of the system is possible as it would allow the attacker to modify system settings, create or modify user accounts, install or remove software, and more.
Microsoft mentions two mitigating factors in the security advisory. A non-administrative user level of the logged in user may impact the effect on the system. In addition, Microsoft EMET, the company's Enhanced Mitigation Experience Toolkit, helps mitigate the attack according to Microsoft provided that it is configured correctly to work with the Internet Explorer web browser.
Download links for all supported operating systems are listed on the security bulletin page on the Microsoft website. To download the update manually, locate the installed version of Internet Explorer under affected software, and click on the link next to the operating system the computer us running on.
This is the second emergency patch released in the past couple of weeks. Microsoft released the bulletin MS15-078 in late July for all supported operating systems that addresses a critical vulnerability in Microsoft Font Driver.
 Phenquestions
Phenquestions